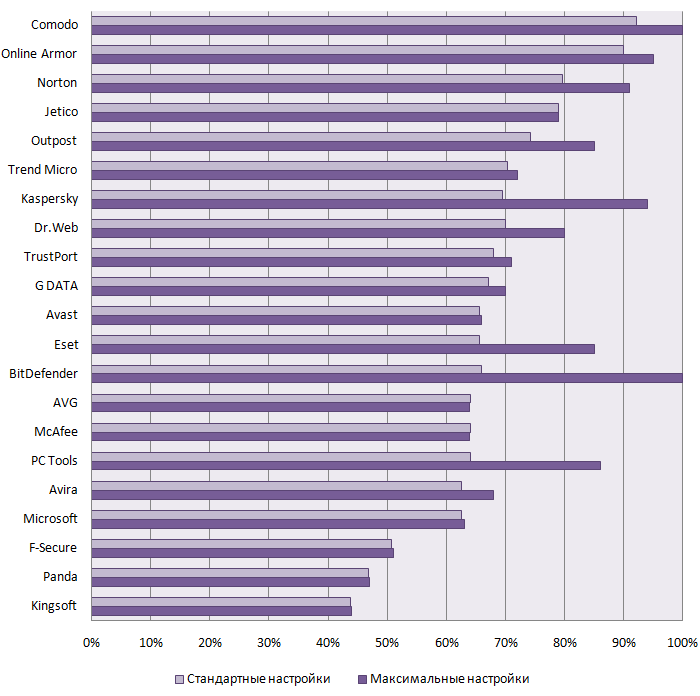
Packers support tests
This test determines which antivirus programs provide their users with the most effective protection from virus modifications created by virus writers who use various compression utilities (packers).
A virus that is known to an antivirus program but is compressed using a different packer becomes undetectable to the solution if it does not support the packer used by the virus writer.
One of the objectives of this test was also to attract the attention of the Internet community to the serious problem posed by the use of packers and other means of protection used by virus writers.

 Malware-writers often use packers (or couple of packers) to impede detection of their "creations" for anti-virus engines. This fact forces antivirus developers to provide operational packers support to make av-engines more powerful for recognizing known malwares under new variants of packers. So, our test will show which AV companies attend to packers support and which not.
Malware-writers often use packers (or couple of packers) to impede detection of their "creations" for anti-virus engines. This fact forces antivirus developers to provide operational packers support to make av-engines more powerful for recognizing known malwares under new variants of packers. So, our test will show which AV companies attend to packers support and which not.