Anti-Rootkit Test for Malware Detection and Removal (April 2010)
Table of Contents:
- Introduction
- Test Results and Awards
Introduction
In these days, rootkit technologies are gaining more and more popularity with virus writers. The cause for this is quite obvious: they make it possible to hide malware and its components from PC users and antivirus programs. You can find the source codes for ready-made rootkits easily in the Internet free access that inevitably brings about widespread of this technology in various Trojan software or spywares.
Rootkit (from the English root kit) is software for hiding the malefactor’s or malware presence traces in the system. Rootkit technologies allow the malware to hide its activity in the victim’s computer by disguising the files, processes as well as its presence in the system.
A lot of specialized software products known as anti-rootkits exist for malware detecting and removing.
The aim of this test is to evaluate the ability of the most popular antivirus and anti-rootkit products to detect and remove malicious programs (‘in-the-wild’ samples) that use rootkit technologies and actively circulate over the Internet. Wide-spread ITW malware testing gives us a good idea of how well the antirootkit software under analysis can cope with well-known rootkits.
It should be noted that although testing of in-the-wild malware samples is of real practical use, there is also a great deal of research value in ascertaining the capabilities of proactive detection when combating the hidden threat of rootkits.
- Methodology of Anti-Rootkits Test for Malware Detection and Removal »
- Awards Guide for Rootkits Detection and Removal Test »
12 specialized anti-rootkits selected in accordance with the methodology took part in the test:
- Eset SysInspector 1.2.012.0
- GMER 1.0.15.15281
- KernelDetective 1.3.1
- Online Solutions Autorun Manager 5.0.11922.0
- Panda Anti-Rootkit 1.0.8.0
- Sophos Anti-Rootkit 1.5.0
- SysReveal 1.0.0.27
- Rootkit Unhooker 3.8.386.589
- RootRepeal 1.3.5
- Trend Micro RootkitBuster 2.80
- VBA32 Antirootkit 3.12 (beta)
- XueTr 1.0.2.0
The test was conducted using six malicious programs, each of them using its own disguising method in the system. The sample kit is formed in strict accordance with the definite demands the principal of which was coverage of all masking methods in the system.
Malwares selected for the test:
- TDL (TDSS, Alureon, Tidserv)
- Sinowal (Mebroot)
- Pandex (Rootkit.Protector, Cutwail)
- Rootkit.Podnuha (Boaxxe)
- Rustock (NewRest)
- Srizbi
- Synsenddrv (Rootkit.Pakes, BlackEnergy)
- TDL2 (TDSS, Alureon, Tidserv)
- Max++ (Zero Access)
- Virus.Protector (Kobcka, Neprodoor)
- TDL3 (TDSS, Alureon, Tidserv)
- z00clicker
The test was performed on a PC with Windows XP SP3 and all updates downloaded from March 5 to March 20, 2010 in strict accordance with the definite methodology.
Test Results and Awards
Tables 1-2 show the results of detecting malwares using rootkit technologies with specialized anti-rootkits.
We would like to remind that in accordance with the award scheme, 0.5 points are awarded for every positive result (+, +/+, +/- or -/+ in the Table).
Table 1: Anti-rootkits test results (beginning)
Anti-rootkit / malware |
TDL | Sinowal | Pandex | |||
| Removing file / key registry | Detection | Detection | Restore MBR | Removing file / key registry | Detection | |
| GMER | +/- | + | + | - | +/+ | + |
| KernelDetective | +/- | + | - | - | +/- | + |
| OSAM | +/+ | + | - | - | +/+ | + |
| Panda Anti-Rootkit | -/- | - | - | - | -/- | - |
| Rootkit Unhooker | +/- | + | + | - | BSOD | |
| RootRepeal | +/+ | + | + | + | +/+ | + |
| Sophos Anti-Rootkit | +/- | + | - | - | -/- | + |
| Eset SysInspector | -/- | + | - | - | -/- | + |
| SysReveal | +/+ | + | - | - | -/+ | + |
| Trend Micro RootkitBuster | -/- | + | + | - | -/- | - |
| VBA32 Antirootkit | +/- | + | + | - | +/+ | + |
| XueTr | +/- | + | - | - | +/+ | + |
It is quite obvious from Table 1 that most products testes experienced great difficulties with Sinowal (Mebroot) bootkit. Only four of anti-rootkits tested managed to detect it and RootRepeas was the only one that managed to restore MBR. Panda Anti-Rootkit that won no points at all turned out the most helpless of the set of three rootkits.
Table 2: Anti-rootkits test results (end)
| Anti-rootkit / malware | Podnuha | Rustock | Srizbi | |||
| Removing file / key registry | Detection | Removing file / key registry | Detection | Removing file / key registry | Detection | |
| GMER | +/+ | + | -/- | + | +/+ | + |
| KernelDetective | +/- | + | +/- | + | +/- | + |
| OSAM | +/+ | + | +/+ | + | +/+ | + |
| Panda Anti-Rootkit | -/- | - | -/- | - | -/- | + |
| Rootkit Unhooker | +/- | + | -/- | + | +/- | + |
| RootRepeal | +/+ | + | -/- | + | +/+ | + |
| Sophos Anti-Rootkit | -/- | + | -/- | + | -/- | + |
| Eset SysInspector | -/- | + | -/- | - | -/- | + |
| SysReveal | -/+ | + | -/- | + | +/+ | + |
| Trend Micro RootkitBuster | -/- | - | -/- | - | -/- | + |
| VBA32 Antirootkit | +/- | + | -/- | + | +/- | + |
| XueTr | +/+ | + | -/- | + | +/+ | + |
Table 2 suggests several conclusions. The first one is that Rustock (NewRest) rootkit is practically anassailable as KernelDetective and Online Solutions Autorun Manager (OSAM) were the only ones that managed to clean it. On the whole, there were hardly any problems with detecting this rootkit set except for outsiders like Panda Anti-Rootkit and Trend Micro RottkitButster that won only 0.5 points for detecting Srizbi.
Table 3: Anti-rootkits test results (continued)
| Anti-rootkit / malware | Synsenddrv | TDL2 | Max++ | |||
| Removing file / key registry | Detection | Removing file / key registry | Detection | Detection | Copying infected driver | |
| GMER | +/+ | + | +/+ | + | + | + |
| KernelDetective | +/- | + | -/- | + | - | - |
| OSAM | +/+ | + | Can't read the file | + | + | |
| Panda Anti-Rootkit | +/+ | + | -/- | - | - | - |
| Rootkit Unhooker | +/- | + | -/- | + | - | + |
| RootRepeal | +/+ | + | +/+ | + | - | + |
| Sophos Anti-Rootkit | +/- | + | +/- | + | + | - |
| Eset SysInspector | -/- | + | -/- | - | - | - |
| SysReveal | -/- | + | -/- | + | - | - |
| Trend Micro RootkitBuster | +/+ | + | -/- | + | - | - |
| VBA32 Antirootkit | +/- | + | -/- | - | + | + |
| XueTr | +/+ | + | +/- | + | - | - |
Synsenddrv (Rootkit.Pakes, BlackEnergy) turned to be the easiest from the malware set for being detected and removed: all the tested anti-rootkits managed to detect it and Eset SysInspector and SysReveal were the only ones that failed to neutralize it. Max++ (ZeroAcess) caused the biggest difficulties from the whole set as only four products managed to detect it and two more managed to copy the infected driver.
Table 4: Anti-rootkits test results (end)
| Anti-rootkit / malware | Protector | TDL3 | z00clicker | |||
| Detection | Copying infected driver |
Detection | Copying infected driver | Detection |
Copying infected driver |
|
| GMER | + | + | + | - | + | + |
| KernelDetective | + | + | - | - | - | - |
| OSAM | + | + | - | - | - | - |
| Panda Anti-Rootkit | - | - | - | - | - | - |
| Rootkit Unhooker | + | + | + | - | - | - |
| RootRepeal | + | + | - | - | - | - |
| Sophos Anti-Rootkit | + | - | - | - | - | - |
| Eset SysInspector | - | - | - | - | - | - |
| SysReveal | + | + | - | - | - | - |
| Trend Micro RootkitBuster | - | - | - | - | - | - |
| VBA32 Antirootkit | + | + | + | + | + | + |
| XueTr | + | + | + | - | - | - |
As we can see from Table 4, this is the rootkit set that caused the biggest problems with the products tested especially with TDL3 (TDSS, Alureon, Tidserv) and z00clicker. GMER and VBA32 Antirootkit proved themselves to be better than the other ones that lost a lot of points. Eset SysInspector, Trend Micro RootkitBuster and Panda Anti-Rootkit detected nothing from that set.
Summarizing all the data provided in Tables 1-4, we can get the final results for the tested anti-rootkits efficiency (on the basis of maximum 12 points), see Diagram 1 and Table 5.
Diagram 1: Results of Anti-Rootkit Test (points awarded)
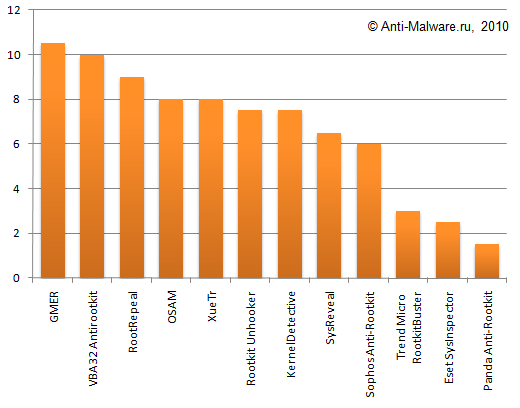
Table 5: The best anti-rootkits based on the test results
|
Anti-rootkit
|
Award |
Total points |
% of max points |
|
GMER 1.0.15.15281 |
Gold Anti-Rootkit |
10,5 |
88% |
|
VBA32 Antirootkit 3.12 (beta) |
10 |
83% |
|
|
RootRepeal 1.3.5 |
Silver Anti-Rootkit |
9 |
75% |
|
Online Solutions Autorun Manager 5.0.11922.0 |
8 |
67% |
|
|
XueTr 1.0.2.0 |
8 |
67% |
|
|
Rootkit Unhooker 3.8.386.589 |
7,5 |
63% |
|
|
KernelDetective 1.3.1 |
7,5 |
50% |
|
|
SysReveal 1.0.0.27 |
Bronze Anti-Rootkit |
6,5 |
54% |
|
Sophos Anti-Rootkit 1.5.0 |
6 |
50% |
|
|
Trend Micro RootkitBuster 2.80 |
Failed |
3 |
25% |
|
Eset SysInspector 1.2.012.0 |
2,5 |
21% |
|
|
Panda Anti-Rootkit 1.0.8.0 |
1,5 |
13% |
By the test results, GMER and VBA32 Antirootkit were considered the best anti-rootkits that justly receive Gold Anti-Rootkit Protection Award. You can their superiority over the others from the last three rootkit samples in Table 4.
RootRepeal, Online Solutions Autorun Manager (OSAM), XueTr, Rootkit Unhooker (unfortunately it has not been actively developing and lost its leadership by our test results) and KernelDetective showed very good results. Это продукты получают награду Silver Anti-Rootkit Protection Award.
SysReveal and Sophos Anti-Rootkit showed satisfactory results and won Bronze Anti-Rootkit Protection Award. If the last Sophos product is not actively developing, the first two have a good chance to improve their results in the future tests.
Grigoriy Smirnov, Testing Engineer, Anti-Malware Test Lab, comments the test results as follows:
“Having brought our testing to the logical end we obtained a detailed picture of modern anti-rootkits abilities on removing complicated malware ITW-samples using rootkit technologies. On the basis of the results obtained we can come to the conclusions that antivirus vendors whose products participated in the testing just pretend they can offer solutions for complicated threats liquidation. In fact most of the vendors' anti-rootkits cannot resist modern rootkits because of their technical weakness that is proved by our tests. VBA32 AntiRootkit by VirusBlockAda is a positive exception from this picture. This product managed to detect the most complicated infections using system drivers patching. This result is undoubtedly an evidence of this solution high predictability. Keep it up! But Gmer – the winner of this testing is also worth mentioning. I think this product has always been a model among rootkits.
Such solutions as OSAM, Xuetr, KernelDetective and RootRepeal showed great results that are quite natural as all these anti-rootkits are actively supported by their designers. As we know, RKU stopped being publicly supported, thus, the results were not as good as with the current leaders.
And I would like to mention separately that only OSAM and KernelDetective managed to neutralize Rustock in our test. RootRepeal is also worth special attention as this anti-rootkit managed to restore infected MBR. In the conclusion it is worth mentioning that all anti-rootkit vendors have a lot of things to think over at the preset. Virus writing never remains in the same place and is constantly developing. And that is the thing we would like to have from specialized anti-rootkits.”
Vasiliy Berdnikov, Head of Testing Department, Anti-Malware Test Lab, comments the test results as follows:
A lot of new rootkits appeared in the way of applied technologies during the last year. One of them is TDL2 with the mechanism of protection from its detection and removal (blocking the disk and volume opening, tap recreating, tracking the driver loading order). New Rustock rootkit modifications also appeared that is cable of recreating IRP- and DKOH-taps in case of unloading that we could not observe in other malware families before (IRP-hooks also recreates Pandex). Rootkits max++ and TDL3 appeared relatively recently patching system drives and storing their components outside an infected PC file system.
At the same time, virus makers go deeper and deeper inside the system and anti-rootkit software developers have to trace the latest rootkit development tendencies in order not to lag behind. The test results prove obviously that the most actively developing anti-rootkits such as Gmer, VBA32, AntiRootkit, RootRepeal, OSAM, Xuetr, RKU and KernelDetective are the most successful in fighting modern rootkits.
To study the detailed results of this test and make sure of the final calculations correctness we recommend downloading the test results in Microsoft Excel format.
Complete testing results in Microsoft Excel format »
- Login to post comments