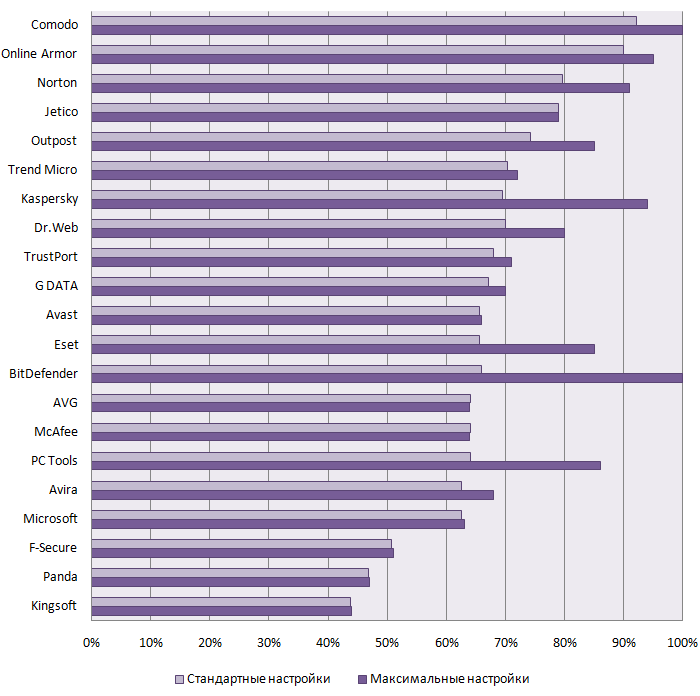
Active Malware Treatment Test (October 2008)
Table of Contents:
- Introduction
- Test Results and Awards
- Analysis of Changes to Previous Tests
Introduction
Take a good look at the results of any antivirus product protection quality test and you are unlikely to see a result of 100% in the test charts. Even the best antivirus solutions are sometimes unable to detect a malicious program the moment it enters a computer. This is hardly surprising, since in recent years the growth in the number of viruses and the speed with which they spread has resembled an avalanche.
But don’t panic – today’s antivirus programs have a variety of tools for combating malicious programs even in the event that they have made their way on to your computer. Keep in mind, though, that malicious programs are good at masking their presence on your system, making the antivirus program’s job even harder.
This is not the first time the Anti-Malware Test Lab has tested antivirus products for their ability to combat malicious programs in just this kind of situation, when they have already penetrated your computer and started their activity, while masking their presence on the system. Will antivirus solutions be able to detect and remove the malicious program without disrupting the system’s operation? This test will show how popular antivirus products cope with this difficult task.
Methodology for Active Malware Treatment Tests »
Awards Guides of Active Malware Treatment Test»
The following antivirus products were tested:
- Avast! Professional Edition 4.8.1229
- AVG Anti-Virus & Anti-Spyware 8.0.0.2
- Avira AntiVir PE Premium 8.1.0.367
- BitDefender Antivirus 2009 (12.0.10.1)
- Dr.Web Anti-Virus 4.44.5.8080
- Eset NOD32 Antivirus 3.0.669.0
- F-Secure Anti-Virus 2009
- Kaspersky Anti-Virus 2009 (8.0.0.357)
- McAfee VirusScan 2008 (12.1.110)
- Outpost Antivirus Pro 6.5.2358.316.0607
- Panda Antivirus 2009
- Sophos Antivirus 7.3.4
- Norton AntiVirus 2009
- Trend Micro Antivirus plus Antispyware 2008 (16.10.1182)
- VBA32 Antivirus 3.12.8.6
The malicious programs used in the test were selected based on a set of criteria developed by the testing team. The following malicious programs were used (names are given according to the Kaspersky Lab classification):
- Adware. Win32.NewDotNet
- Backdoor.Win32.Sinowal.ce
- Email-Worm.Win32.Scano.bd
- Rootkit.Win32.Agent.ea
- Rootkit.Win32.Podnuha.a
- Trojan-Dropper.Win32.Agent.vug
- Trojan-Dropper.Win32.Mutant.e
- Trojan-Proxy.Win32.Saturn.cu
- Trojan-Proxy. Win32.Xorpix.dh
- Trojan-Spy.Win32.Zbot.bsa
- Trojan.Win32.Agent.lkz
- Trojan.Win32.Monderb.gen
- Trojan.Win32.Pakes.cuh
- Trojan.Win32.Small.yc
- Virus.Win32.Rustock.a
Active infection treatment capabilities of antivirus products were tested in strict accordance with the methodology developed by the testing team.
Test Results and Awards
Table 1: Active infection treatment results for different antivirus products (part 1)
| Malicious programs / Antivirus products |
Avast! Professional Edition | AVG Anti-Virus & Anti-Spyware | Avira AntiVir PE Premium | BitDefender Antivirus | Dr.Web Anti-Virus |
| Adware. Win32.NewDotNet | + | - | - | + | + |
| Backdoor.Win32.Sinowal.ce | + | - | - | - | + |
| Email-Worm.Win32.Scano.bd | - | - | - | - | + |
| Rootkit.Win32.Agent.ea | + | - | - | + | + |
| Rootkit.Win32.Podnuha.a | + | - | - | - | + |
| Trojan-Dropper.Win32.Agent.vug | + | + | + | - | + |
| Trojan-Dropper.Win32.Mutant.e | + | - | - | - | + |
| Trojan-Proxy.Win32.Saturn.cu | + | - | - | - | + |
| Trojan-Proxy. Win32.Xorpix.dh | + | + | - | - | + |
| Trojan-Spy.Win32.Zbot.bsa | + | + | + | + | + |
| Trojan.Win32.Agent.lkz | + | + | - | + | + |
| Trojan.Win32.Monderb.gen | + | + | + | + | + |
| Trojan.Win32.Pakes.cuh | + | + | |||
| Trojan.Win32.Small.yc | - | - | - | - | + |
| Virus.Win32.Rustock.a | - | - | - | - | + |
| Removed/Total | 12/15 | 5/15 | 3/15 | 5/15 | 15/15 |
Table 2: Active infection treatment results for different antivirus products (part 2)
| Malicious programs / Antivirus products |
Eset NOD32 Antivirus |
F-Secure Anti-Virus |
Kaspersky Anti-Virus |
McAfee VirusScan |
Outpost Antivirus Pro |
| Adware. Win32.NewDotNet | - | - | + | + | + |
| Backdoor.Win32.Sinowal.ce | - | - | + | + | - |
| Email-Worm.Win32.Scano.bd | - | - | + | - | - |
| Rootkit.Win32.Agent.ea | - | - | - | - | - |
| Rootkit.Win32.Podnuha.a | - | - | + | - | - |
| Trojan-Dropper.Win32.Agent.vug | - | + | + | - | + |
| Trojan-Dropper.Win32.Mutant.e | - | + | + | + | - |
| Trojan-Proxy.Win32.Saturn.cu | - | - | - | - | + |
| Trojan-Proxy. Win32.Xorpix.dh | - | + | + | - | + |
| Trojan-Spy.Win32.Zbot.bsa | - | - | + | + | + |
| Trojan.Win32.Agent.lkz | - | + | + | + | + |
| Trojan.Win32.Monderb.gen | - | + | + | - | + |
| Trojan.Win32.Pakes.cuh | - | - | - | + | |
| Trojan.Win32.Small.yc | - | - | + | - | - |
| Virus.Win32.Rustock.a | - | - | + | - | - |
| Removed/Total | 0/15 | 5/15 | 12/15 | 5/15 | 8/15 |
Table 3: Active infection treatment results for different antivirus products (part 3)
| Malicious programs / Antivirus products |
Panda Antivirus |
Sophos Anti-Virus |
Norton AntiVirus | Trend Micro Antivirus plus Antispyware | VBA32 Antivirus |
| Adware. Win32.NewDotNet | + | + | + | + | - |
| Backdoor.Win32.Sinowal.ce | - | - | - | - | - |
| Email-Worm.Win32.Scano.bd | - | - | + | - | - |
| Rootkit.Win32.Agent.ea | - | - | - | - | - |
| Rootkit.Win32.Podnuha.a | - | - | - | - | - |
| Trojan-Dropper.Win32.Agent.vug | + | - | + | + | - |
| Trojan-Dropper.Win32.Mutant.e | - | - | + | - | - |
| Trojan-Proxy.Win32.Saturn.cu | - | - | - | - | - |
| Trojan-Proxy. Win32.Xorpix.dh | + | - | + | + | - |
| Trojan-Spy.Win32.Zbot.bsa | + | - | + | - | - |
| Trojan.Win32.Agent.lkz | + | - | + | + | - |
| Trojan.Win32.Monderb.gen | + | - | + | + | - |
| Trojan.Win32.Pakes.cuh | - | - | - | - | - |
| Trojan.Win32.Small.yc | - | + | - | - | - |
| Virus.Win32.Rustock.a | - | - | - | - | - |
| Removed/Total | 6/15 | 2/15 | 8/15 | 5/15 | 0/15 |
Notice! According to analysis of testing results and awards:
( + ) means that antivirus solution successfully removed the active infection, and the system was restored (or was not damaged),
( - ) The antivirus solution failed to remove the active infection or the system’s integrity was seriously damaged.
As Tables 1 through 3 demonstrate, the hardest virus to remove was Virus.Win32.Rustock.a, which was successfully removed only by Dr.Web Anti-Virus and Kaspersky Anti-Virus.
In terms of difficulty of removal, Rustock is followed by three Trojan programs: Trojan-Proxy.Win32.Saturn.cu, Trojan.Win32.Pakes.cuh and Trojan.Win32.Small.yc and two rootkits – Rootkit.Win32.Agent.ea and Rootkit.Win32.Podnuha.a. Each of these malicious programs was removed by three antivirus products only. It is worth noting that only Dr.Web Anti-Virus and Avast got the better of both rootkits.
Email-Worm.Win32.Scano.bd was equally difficult to remove: only three products (Dr.Web Anti-Virus, Kaspersky Anti-Virus and Norton AntiVirus) were successful in removing it. Interestingly, worms from this family were used in the first of our active infection treatment tests. The situation has not improved in the year and a half since that test.
The Trojan-spy Backdoor.Win32.Sinowal.ce, which modifies the master boot record (MBR) of the hard drive, submitted to four antivirus products: Avast, Dr.Web Anti-Virus, Kaspersky Anti-Virus and McAfee.
As the results table above shows, only six out of the 15 antivirus products tested demonstrated an acceptable active infection treatment performance.
Dr.Web Anti-Virus, which successfully removed all 15 malicious programs from the system, is the clear winner. This is the first antivirus product to win the Platinum Malware Treatment Award. Two more antivirus solutions – Kaspersky Anti-Virus and Avast! – also put in an excellent performance and earned the Gold Malware Treatment Award.
Outpost Antivirus Pro, Norton AntiVirus and Panda Antivirus also demonstrated good results and received well-deserved Bronze Malware Treatment Awards. Unfortunately, the test results for the other antivirus products were less than satisfactory. These products cannot be considered effective at treating infected computers.
It is worth mentioning the unexpectedly high result achieved by Avast!, which had previously not demonstrated such good results in the treatment of difficult infections, as well as the successful début of Outpost Antivirus Pro.
To view detailed results of the test and verify our calculations, you can download test results in Microsoft Excel.
Analysis of Changes to Previous Tests
We decided to analyze the results of all our active infection tests conducted during 2007 and 2008. To do this, we compared the results of this test with those conducted in February 2008 and September 2007.
This enabled us to visualize how the effectiveness of complicated infection treatment changed over time for each product tested (with the exception of Outpost Antivirus, which was not included in the previous two tests) – see Figure 1.
Figure 1: Changes in active infection treatment capabilities of antivirus products
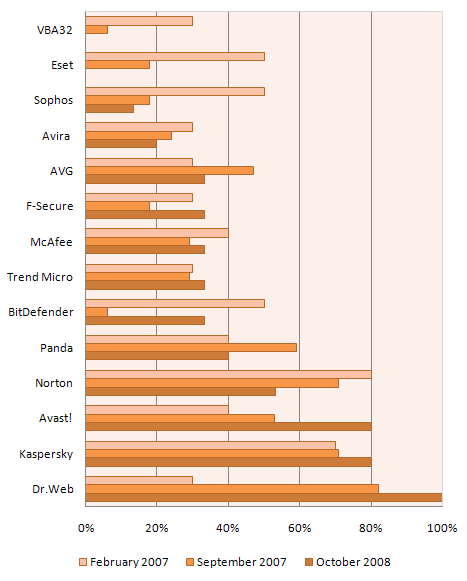
Figure 2: Changes in active infection treatment capabilities of antivirus products
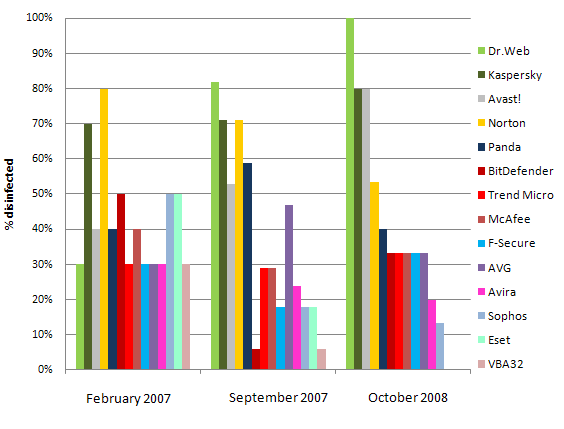
As Figures 1 and 2 demonstrate, only Avast, Kaspersky Anti-Virus and Dr.Web Anti-Virus have improved their results from one test to the next. The results of other antivirus products have either remained unsatisfactory or – even worse for users – have deteriorated.
Vasily Berdnikov, an expert from Anti-Malware Test Lab and the coordinator of this test, provided the following comments on the test results:
“The number of malicious programs that use active protection from detection and removal is constantly growing. This is because it is essential to virus writers to make their creations invisible to users to ensure that they keep functioning on infected systems, performing their malicious functions for as long as possible. If you look at the latest trends in the development of such programs, you will see that virus writers are gradually evolving from masking malware files on the hard drive to blocking attempts by antivirus programs to read malicious files or extract their original content.
Whereas before malicious programs were masked from antivirus products and users by altering function addresses in the System Service Descriptor Table, now a more commonly used approach is to use function hooks that are based on modifying function machine code, since they are harder to detect. Other commonly used methods include hooking IRP handlers for disk or file system drivers. Antivirus developers should give a higher priority to the combating of new types of malicious programs that are active on the system. Otherwise, they risk falling far behind in terms of technological development.”
- Login to post comments